Transformative Potential: Edge AI in Edge Computing
Edge AI, the integration of artificial intelligence algorithms into edge computing systems, represents a significant leap forward in the realm of computing technologies. This fusion of AI and edge computing unlocks new capabilities, reshaping data processing, and empowering devices at the edge of networks.
The Synergy of Edge Computing and AI
Edge computing brings computation closer to data sources, reducing latency and enhancing real-time processing. The integration of AI at the edge empowers devices to perform complex analytics and decision-making locally, minimizing the need for continuous data transfer to centralized servers.
The convergence of Edge AI in Edge Computing marks a pivotal shift in technological capabilities. This platform serves as an informative nexus, showcasing the synergy between edge computing and AI, elucidating the applications and advancements in this domain.
Real-Time Data Processing and Analytics
Edge AI enables real-time data processing and analytics, crucial for applications where latency is a critical factor. From smart cities managing traffic flows to industrial machinery optimizing operations, the ability to process and act on data instantaneously is invaluable.
Enhancing Device Autonomy and Efficiency
By embedding AI capabilities into edge devices, autonomy and efficiency are enhanced. Devices can make decisions locally, reducing dependency on continuous network connectivity. This autonomy streamlines operations, especially in scenarios with limited bandwidth or intermittent connectivity.
Addressing Data Privacy and Security
Edge AI promotes data privacy by processing sensitive information locally without transmitting it to external servers. This localized approach enhances security, mitigating risks associated with transmitting sensitive data over networks, bolstering privacy and compliance.
The platform of Edge AI in Edge Computing demystifies the fusion of AI and edge technologies. It acts as a knowledge center, unveiling the potential and challenges associated with deploying AI at the edge of networks.
Challenges and Adaptability
Despite its potential, integrating AI at the edge presents challenges like limited resources and heterogeneous environments. Innovations addressing these challenges are vital for broader adoption and seamless integration into diverse edge ecosystems Edge AI .
Future Visions: AI at the Edge
Looking ahead, the future of AI in edge computing is promising. Advancements in AI algorithms, coupled with edge computing infrastructures, will drive innovation across industries, unlocking new possibilities for real-time analytics, automation, and decision-making.
Edge AI in Edge Computing encapsulates the paradigm shift in computing landscapes. It underscores the fusion of AI and edge technologies, redefining how data is processed, decisions are made, and devices operate on the periphery of networks.


Securing Edge Computing: Enhanced Safety
Edge computing, a transformative technology, brings computing resources closer to data sources, offering agility and speed in data processing. However, with its benefits come crucial considerations in ensuring robust security measures.
Understanding Edge Computing
Edge computing decentralizes data processing, enabling computation and storage closer to the data source rather than in a centralized cloud. This proximity reduces latency and enhances real-time data analysis, revolutionizing various industries, including IoT, healthcare, and autonomous vehicles.
Unique Security Challenges
The distributed nature of edge computing introduces unique security challenges. Securing a multitude of devices and endpoints scattered across diverse locations demands a comprehensive security strategy. Addressing vulnerabilities in these dispersed nodes is critical to prevent potential breaches.
As the landscape of technology evolves, Edge Computing Security emerges as a vital component, offering insights and strategies to fortify the security of edge computing environments.
Ensuring Data Integrity and Privacy
Protecting data integrity and user privacy is paramount in edge computing. With data processing occurring closer to devices, ensuring encryption, secure transmission, and access control measures becomes crucial to safeguard sensitive information.
Edge Security Architecture
Establishing a robust security architecture for edge computing involves implementing layers of defense mechanisms. This includes identity management, encryption, intrusion detection systems, and continuous monitoring to detect and respond to security threats promptly.
Collaborative Efforts and Standardization
The complexity of edge computing security calls for collaborative efforts among industry players to establish standardized security protocols. Creating cohesive frameworks and best practices promotes interoperability and enhances the overall security posture.
Regulatory Compliance and Governance
Navigating regulatory frameworks is imperative in edge computing. Adhering to data protection regulations and ensuring compliance with privacy laws across multiple jurisdictions is essential for businesses operating within edge computing ecosystems.
As edge computing reshapes technological paradigms, Edge Computing Security serves as a resource hub, shedding light on the complexities and advancements in fortifying the security of edge computing environments.
Continuous Innovation and Adaptability
Continuous innovation in security measures is vital to address evolving threats in edge computing. Research and development efforts focus on enhancing security protocols, threat intelligence, and anomaly detection to stay ahead of potential risks.
The Future of Secure Edge Computing
Securing edge computing is fundamental to realizing its full potential. Platforms like Edge Computing Security drive discussions and innovations, shaping the future landscape of secure edge computing environments.
As technology progresses, the intersection of security and edge computing remains pivotal. Exploring platforms like Edge Computing Security unveils strategies and insights vital to fortify the safety of these distributed computing systems.
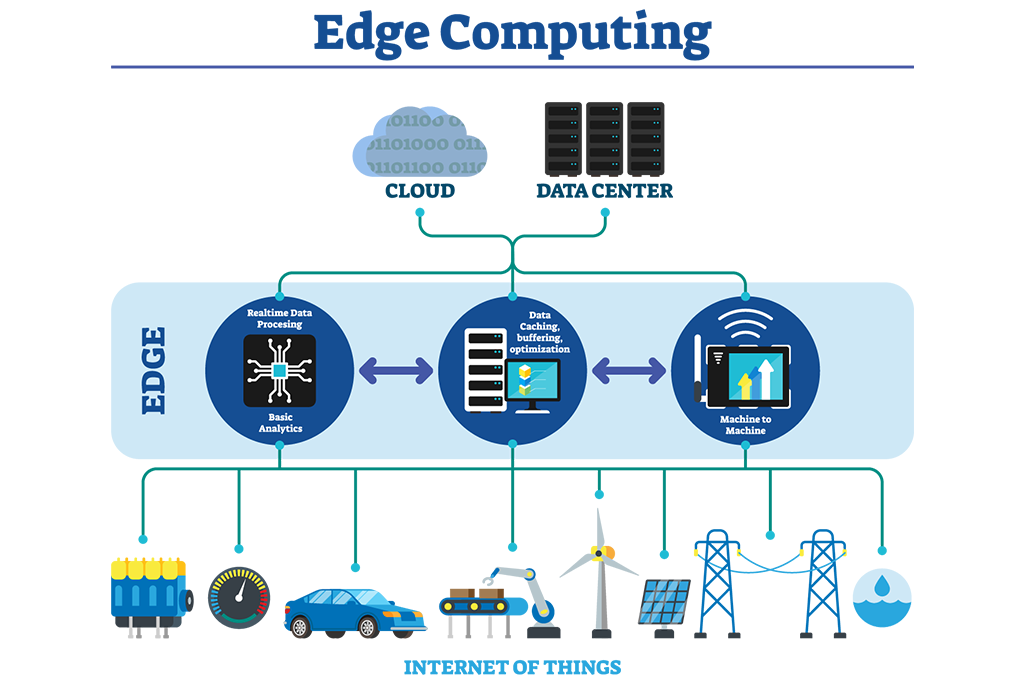

Revolutionizing Retail with Edge Computing: Introduction
In the fast-paced world of retail, staying ahead requires cutting-edge technologies. Edge Computing has emerged as a game-changer, transforming how retailers operate and engage with customers. This article explores the impact of Edge Computing in retail, delving into the innovative solutions that are reshaping the industry.
Optimizing In-Store Operations
Edge Computing brings the power of real-time data processing directly to the edge of the network, optimizing in-store operations. From inventory management to point-of-sale transactions, retailers can leverage Edge Computing to process data locally, reducing latency and enhancing the overall efficiency of in-store processes.
Enabling Personalized Customer Experiences
One of the significant advantages of Edge Computing in retail is its ability to enable personalized customer experiences. By processing and analyzing customer data at the edge, retailers can deliver tailored recommendations, promotions, and services in real-time. This level of personalization enhances customer engagement and satisfaction.
To explore the impact of Edge Computing in retail, visit Edge Computing in Retail. This platform showcases innovative solutions that leverage Edge Computing for a seamless and personalized retail experience.
Enhancing Security and Loss Prevention
Security is a top priority in retail, and Edge Computing plays a vital role in enhancing security measures. By processing video surveillance footage and other sensor data locally, Edge Computing enables quicker response times to security threats. This not only improves loss prevention efforts but also ensures a safer shopping environment for customers.
Powering Smart Shelf Technology
Smart shelf technology is gaining momentum in retail, and Edge Computing is at the core of its functionality. By embedding edge devices on shelves, retailers can monitor product availability, update pricing information in real-time, and even analyze customer interactions with products. This dynamic approach to shelf management improves overall store efficiency.
Efficient Supply Chain Management
Edge Computing revolutionizes supply chain management in retail by providing real-time visibility and control. From tracking the movement of goods to monitoring environmental conditions during transportation, Edge Computing ensures that retailers have accurate and up-to-date information, enabling them to make informed decisions and streamline the supply chain.
Enabling Edge-Powered E-Commerce Platforms
In the digital retail landscape, Edge Computing is instrumental in powering e-commerce platforms. By processing and caching content closer to end-users, retailers can deliver faster load times and a seamless online shopping experience. This edge-powered approach reduces latency, ensuring a responsive and enjoyable customer journey.
Improving Customer Insights and Analytics
Edge Computing enables retailers to gather valuable customer insights and analytics directly from edge devices. By processing data locally, retailers can gain real-time information about customer behavior, preferences, and trends. This data-driven approach enhances decision-making processes and empowers retailers to adapt quickly to changing market dynamics.
Challenges and Considerations in Edge Computing
While Edge Computing offers numerous benefits, it comes with its own set of challenges and considerations. Managing distributed edge infrastructure, ensuring data security and compliance, and addressing interoperability issues are crucial aspects that retailers must navigate to fully harness the potential of Edge Computing.
Future Innovations and Scalability
The future of Edge Computing in retail holds exciting possibilities. As technology continues to evolve, retailers can expect innovations that further enhance the scalability, efficiency, and capabilities of Edge Computing solutions. From augmented reality shopping experiences to AI-driven retail insights, the journey of Edge Computing in retail is an ongoing exploration of new frontiers.
Conclusion: Transforming the Retail Landscape
Edge Computing is undeniably transforming the retail landscape, ushering in an era of enhanced operational efficiency, personalized customer experiences, and innovative solutions. As retailers embrace and integrate Edge Computing into their strategies, they position themselves at the forefront of industry evolution, ready to meet the dynamic demands of the modern retail landscape.
Securing Connected Homes: Introduction
In the era of smart homes, where devices are interconnected for seamless living, the issue of privacy becomes paramount. This article delves into the importance of Smart Home Privacy Solutions, exploring how these solutions address concerns and empower users to enjoy the benefits of a connected home without compromising their privacy.
To explore cutting-edge Smart Home Privacy Solutions, visit Smart Home Privacy Solutions. This platform offers insights into the latest technologies and practices, ensuring a privacy-centric smart home experience.
Data Encryption and Secure Communication
Smart Home Privacy Solutions start with robust data encryption and secure communication protocols. By implementing end-to-end encryption for data transmitted between devices and cloud servers, smart home systems ensure that sensitive information remains private and protected from potential breaches. This foundational privacy measure is essential for creating a secure smart home environment.
User Authentication and Authorization
Ensuring that only authorized users have access to smart home devices is a fundamental aspect of privacy protection. Smart Home Privacy Solutions incorporate robust user authentication methods, such as biometric recognition or secure password protocols. This adds an additional layer of security, preventing unauthorized individuals from gaining control over smart home devices.
Local Processing and Edge Computing
To enhance privacy, Smart Home Privacy Solutions leverage local processing and edge computing capabilities. By processing data locally on the device or at the edge of the network, smart homes can minimize the need to send sensitive information to external servers. This approach reduces the risk of data exposure and ensures that critical operations occur within the confines of the home network.
Privacy-Focused Device Design and Default Settings
Smart Home Privacy Solutions prioritize privacy in device design and default settings. Manufacturers implement privacy-by-design principles, creating devices with built-in features that safeguard user data. Additionally, devices come with privacy-friendly default settings, reducing the likelihood of unintentional data sharing and encouraging users to actively manage their privacy preferences.
Continuous Software Updates and Security Patches
To stay ahead of emerging threats, Smart Home Privacy Solutions emphasize the importance of continuous software updates and security patches. Regular updates ensure that devices are equipped with the latest security enhancements, closing potential vulnerabilities. This proactive approach is essential for maintaining a secure and privacy-respecting smart home ecosystem.
Transparent Data Practices and User Control
Transparency in data practices is a cornerstone of Smart Home Privacy Solutions. Manufacturers and service providers communicate clearly about the types of data collected, how it is used, and with whom it is shared. Additionally, users are granted control over their data, allowing them to customize privacy settings, manage permissions, and make informed decisions about the level of data sharing they are comfortable with.
IoT Security Standards and Certifications
Adherence to established IoT security standards and certifications is a key aspect of Smart Home Privacy Solutions. Devices that meet recognized security standards provide users with confidence in the product’s privacy and security features. Certifications from reputable organizations signal that the device has undergone rigorous testing and complies with industry best practices.
User Education and Awareness
Smart Home Privacy Solutions extend beyond technology to include user education and awareness. Manufacturers and service providers actively educate users about privacy best practices, potential risks, and how to maximize privacy settings. This proactive approach empowers users to make informed decisions and actively participate in securing their smart homes.
Legal and Regulatory Compliance
Smart Home Privacy Solutions align with legal and regulatory frameworks to ensure compliance with privacy laws. Manufacturers and service providers adhere to data protection regulations and industry standards, establishing a legal foundation for privacy protection. This commitment to compliance reinforces user trust in the privacy measures implemented in smart home ecosystems.
Building a Privacy-Centric Smart Home Culture
Ultimately, Smart Home Privacy Solutions contribute to building a privacy-centric smart home culture. By prioritizing user privacy, implementing robust security measures, and fostering transparency, the smart home industry can create an environment where users feel confident in adopting connected technologies. This cultural shift is integral to the long-term success and acceptance of smart homes.
Conclusion: Balancing Connectivity and Privacy
Smart Home Privacy Solutions play a vital role in balancing the convenience of connected living with the necessity of privacy protection. As the smart home ecosystem continues to evolve, the integration of advanced privacy measures becomes paramount. By embracing these solutions, users can enjoy the benefits of a smart home while maintaining control over their personal data, ensuring a secure and private living environment.


Securing 5G Networks: Cybersecurity Challenges
The rapid evolution of technology brings the promising era of 5G networks, empowering a world of connectivity and innovation. However, amidst the potential, the landscape of cybersecurity for 5G networks presents formidable challenges that demand robust solutions.
Unprecedented Speed: Vulnerabilities in 5G Infrastructure
The immense speed and capacity offered by 5G networks also introduce vulnerabilities. The architecture’s complexity and the sheer volume of connected devices create a wider attack surface for cyber threats. Securing this intricate web demands a comprehensive approach that addresses potential entry points for malicious actors.
Edge Computing and Security Concerns
Edge computing, a fundamental component of 5G networks, distributes computing closer to data sources. While this enhances speed and efficiency, it also raises concerns regarding data security. Protecting information at the edge demands innovative security protocols to thwart potential breaches and ensure data integrity.
IoT Integration: Strengthening Security Protocols
The integration of the Internet of Things (IoT) into 5G networks amplifies the need for robust security protocols. The vast array of interconnected devices, from smart homes to autonomous vehicles, demands stringent measures to safeguard against cyber threats. Implementing encryption, authentication, and access control becomes paramount to fortify the network.
Network Slicing and Isolation Techniques
Network slicing, a key feature of 5G, allows the creation of multiple virtual networks within a single physical infrastructure. While this enhances network customization, it poses challenges in ensuring the isolation and security of individual slices. Developing sophisticated isolation techniques is crucial to prevent breaches between these segmented networks.
Dynamic Security Measures: Adaptive Defenses for 5G
The dynamic nature of 5G networks necessitates adaptive security measures. Traditional static security solutions may prove inadequate in mitigating evolving threats. Implementing AI-driven security protocols capable of identifying anomalies in real-time becomes imperative to safeguard against sophisticated cyberattacks.
Collaborative Security Ecosystems
The multifaceted nature of 5G cybersecurity demands collaborative efforts across industries and stakeholders. Establishing cohesive security ecosystems that promote information sharing and collective defense strategies is vital. This collaboration can foster the exchange of threat intelligence and best practices to fortify the resilience of 5G networks.
As the realm of technology continues to advance, ensuring the security of 5G networks remains a critical endeavor. Platforms like Cybersecurity for 5G Networks serve as invaluable resources, offering insights and solutions to navigate the complex landscape of securing these next-generation networks. Exploring this platform provides a deeper understanding of the challenges and innovations in fortifying 5G networks against cyber threats, fostering a safer digital environment for all.
- Total visitors : 6,285
- Total page views: 7,971
Recent Posts
- Event Planning and SEO: Making Your Business Visible Online
- Streamlining Reservations and Appointments
- The Backbone of Connected Devices
- Digital Transformation in Government
- Terobosan Terbaru dalam Teknologi Smartphone
- iPhone 15 Inovasi Terbaru dari Apple
- Defining SaaS Companies
- Defining SaaS Companies
- 6 Best Timesheet Management Software for 2024
- How Employees Can Use Employee Monitoring Software to Their Advantage?
- Remote Work Success: How to Create a Mobile Office for Business Trips
- Budget-Friendly Brilliance Best Smartphone Options
- Green Waste-to-Energy Solutions for Sustainability
- Powering the Future Megawatt Electrolyzer Innovations
- Pinnacle of Technology Best Cellphone Choices 2022
- Introducing the Latest New Samsung Phone 2022 Unveiled
- Elevate Your Style Samsung Galaxy 4 Watch Unveiled
- Elevate Your Lifestyle with Apple Watch 7 Cellular
- Elevate Your Mobile Experience with Verizon’s Samsung Phones
- Elevate Your Experience Samsung Galaxy Z Fold3 Unveiled
- Unveiling Samsung Galaxy A7 Lite Compact Powerhouse Tablet
- Get Your Hands on a Free iPhone 13 with Verizon Now!
- Discover the Versatility of Samsung Galaxy Book Go
- Harmonizing Nature and Architecture with Green Walls
- Explore the Best Verizon Android Phones Collection
- Mastering Find My Device Samsung Your Ultimate How-To
- Samsung Galaxy A20 1s Affordable Smartphone Excellence
- Stay Connected in Style with Samsung Galaxy Watch 3
- Unfold the Future Samsung’s Foldable Phone Revealed
- Samsung Galaxy 5 Watch Elevate Your Fitness Journey
Categories
Archives
- October 2024
- September 2024
- August 2024
- July 2024
- June 2024
- May 2024
- April 2024
- February 2024
- January 2024
- December 2023
- September 2023
- August 2023
- July 2023
- June 2023
- May 2023
- April 2023
- March 2023
- February 2023
- January 2023
- December 2022
- November 2022
- October 2022
- September 2022
- August 2022
- July 2022
- June 2022
- August 2021
- July 2021
- June 2021
- May 2021
- April 2021
- March 2021
- February 2021
- January 2021
- December 2020
- November 2020
- October 2020
- September 2020
- August 2020
- July 2020
- June 2020
- May 2020
- April 2020
- March 2020
- February 2020
- January 2020
- July 2019
- December 2016
- November 2016
- October 2016
- September 2016
- August 2016
- July 2016
- June 2016
- May 2016
- April 2016
- March 2016
- February 2016
- January 2016
- December 2015
- November 2015
- October 2015
- September 2015
- August 2015
- July 2015
- June 2015
- May 2015
- April 2015
- March 2015
- February 2015
- January 2015
- December 2014
- November 2014
- October 2014
- September 2014
- August 2014
- July 2014
- June 2014
- May 2014
- April 2014
- March 2014
- February 2014
- January 2014
Partner
ecommerce web design dubai
ecommerce website development dubai
ecommerce website dubai
ecommerce development in dubai
ecommerce development company dubai
ecommerce development company in dubai
ecommerce development dubai
ecommerce website development companies in dubai
ecommerce website development company in dubai
ecommerce website development in dubai
ecommerce website design company near me
ecommerce website design company dubai
ecommerce web development dubai
web ecommerce development
ecommerce website in uae
ecommerce website design dubai
ecommerce web design agency
Partner
app design Dubai
app developers in dubai
app development companies in dubai
app development dubai
application development dubai
app developers uae
app development companies in uae
app development uae
mobile App designer Dubai
mobile App Development Company Dubai
mobile app development company in dubai
mobile app development dubai
mobile application dubai
mobile app development company in uae
mobile app development uae
mobile application development uae
mobile app development company
